Ways To Remove Shortcut Virus Permanently
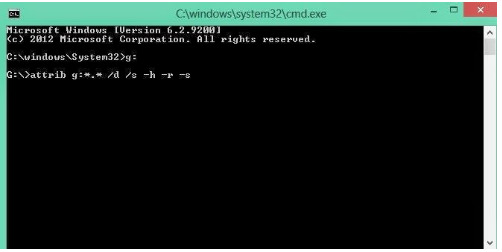
1.Removing Shortcut Virus Using CMD Method (Command Prompt) If you do not wish to install any other shortcut virus remover application , then you can simply remove shortcut virus from your PC/laptop or pendrive by using a command prompt (CMD). Even if you are a non-techy person then also you can easily remove shortcut virus from your pendrive or PC by following the CMD tutorial. Steps To Delete Shortcut Virus By Using CMD: Open command prompt (CMD). (Go to Run >> type CMD >> Hit enter ) Type the drive letter of your removable device and a colon after it and hit enter. (Eg: g: ) Now type: attrib g:*.* /d /s -h -r -s . (Replace g: with the drive name of your drive) Hit enter. Tips To Prevent Shortcut Viruses In Future Prevention is always better than the cure. Its highly recommended to take few precautions to keep your computer away from any kind of shortcut virus or trojans. You should always use updated antivirus and firewalls to keep virus a